How to find personally identifiable information (PII) and secrets exposed by your APIs
As companies grow in size, more and more APIs tend to be added. As these APIs are added, it becomes exponentially more difficult to track how sensitive information flows throughout the code base. Despite best intentions, it can be quite easy for PII or secrets to be accidentally exposed by an API.
Doing a text-based search for sensitive field names such as ssn or dateOfBirth might help you find where that data is – but you might also get a ton of irrelevant results, and you'd definitely miss out on cases where classes create or call out to other classes that have sensitive data.
Fortunately, Moderne offers a recipe that uses rich type information to detect how sensitive data flows throughout your code base. This recipe can detect all sorts of things that a text-based search would fail at. For instance, it can detect if an API returns a class that extends another class that has a method that returns sensitive data – or it can detect when an API returns a class that has a method that returns a different class that has a method that returns sensitive data. It can even recursively step through classes to find sensitive data flow through multiple levels of dependencies.
Let's walk through how to find and use this recipe so you can be more confident that your APIs are not unintentionally exposing sensitive data.
Using the find sensitive API endpoints recipe
-
Navigate to the find sensitive API endpoints recipe.
-
Once there, you'll want to come up with a list of field names that represent PII or secrets for your company. For the purposes of this guide, let's go with these options:
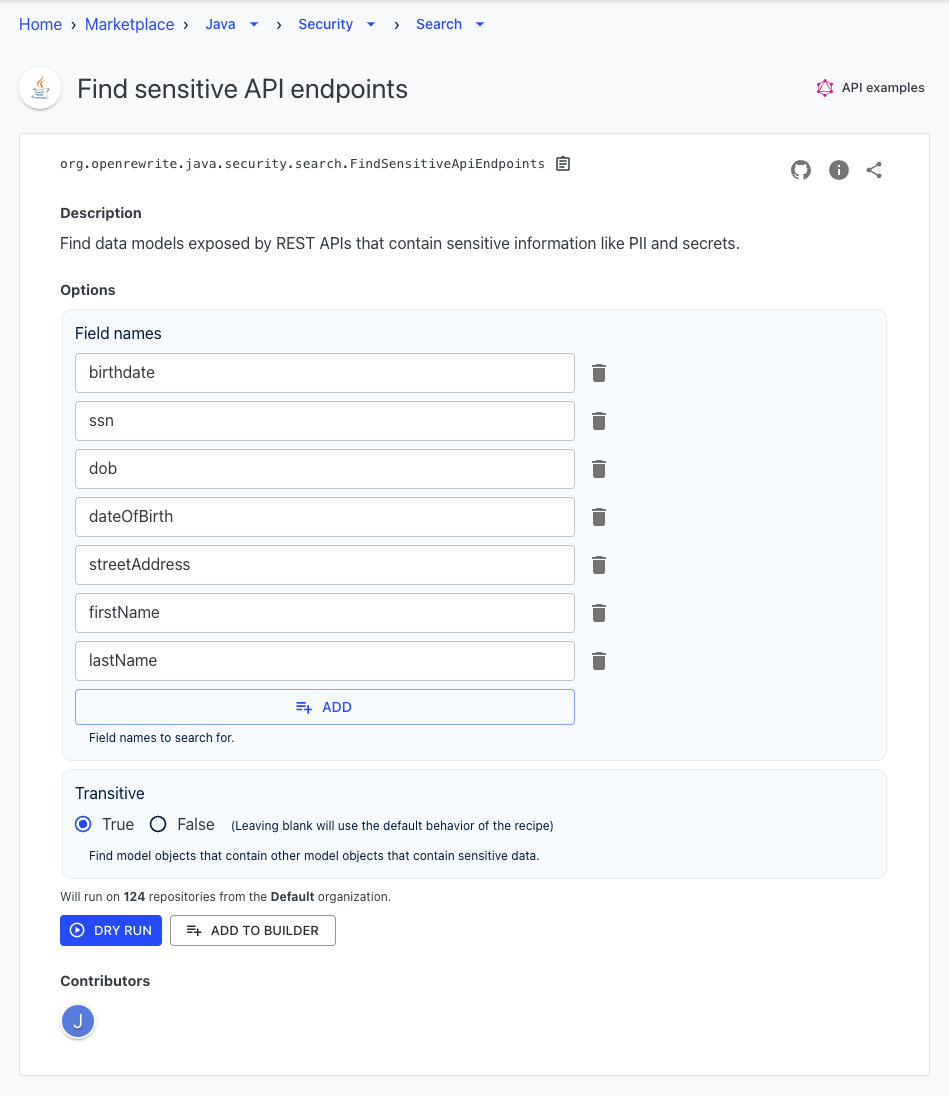
-
After you've come up with the list of field names to search for, you can select whether or not you want the recipe to perform a transitive search. Setting this field to
true(recommended) will recursively check through objects for sensitive data. For instance, if this field istrueand anOwnerobject has agetPetmethod that returns aPetobject that contains PII or secrets (for example,birthDatefrom the options we chose), then the recipe would flag any methods that return anOwnerbecause it could then return aPet. If this field is set tofalse, then the recipe would only check theOwnerclass and any objects theOwnerclass extends (such as aPersonclass). -
Once you've configured the recipe as you want, press the
Dry runbutton and Moderne will begin searching for sensitive APIs. You'll be redirected to a page that looks like this. On the right side of the page, you'll see what APIs returned sensitive information.
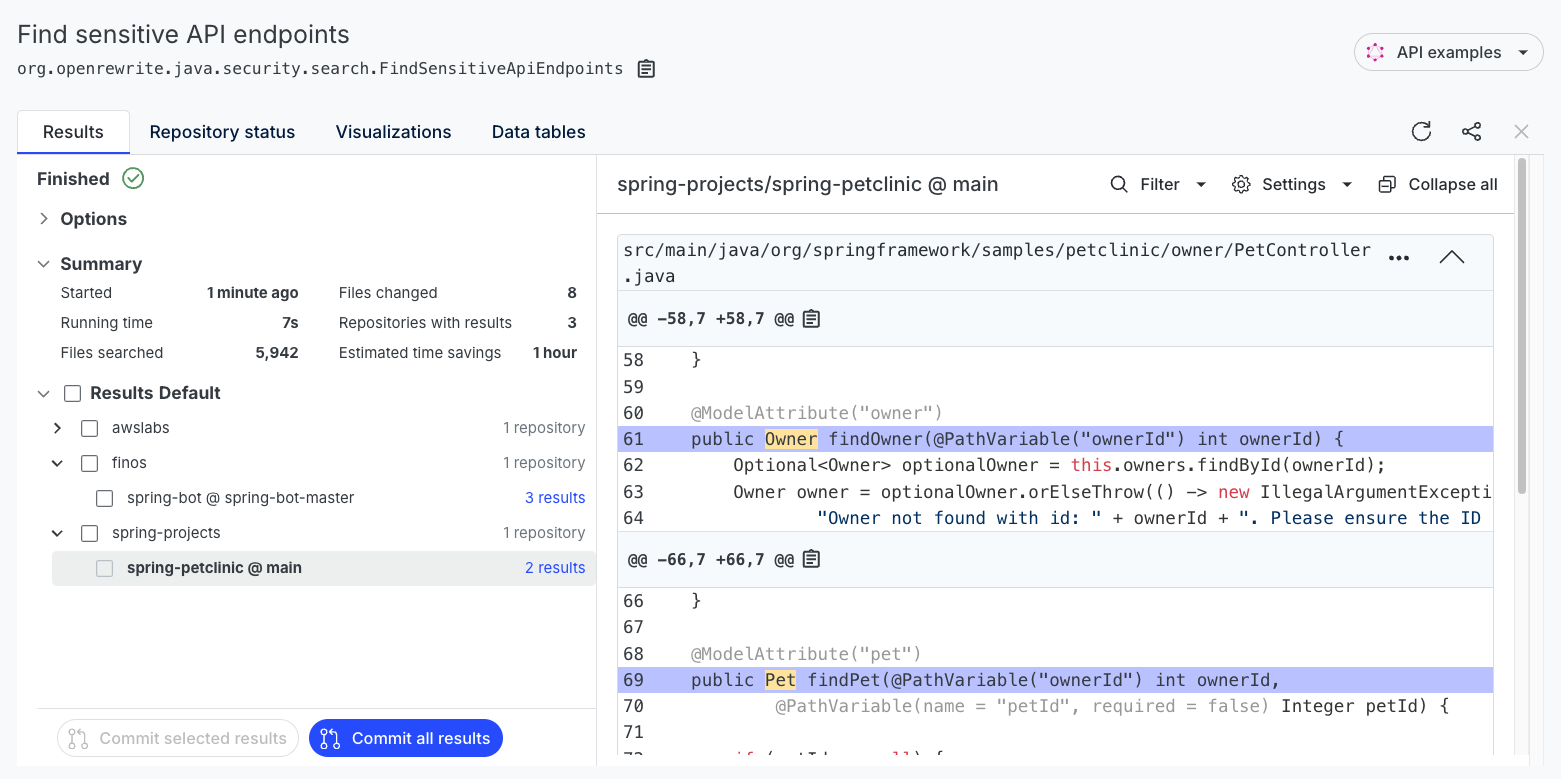
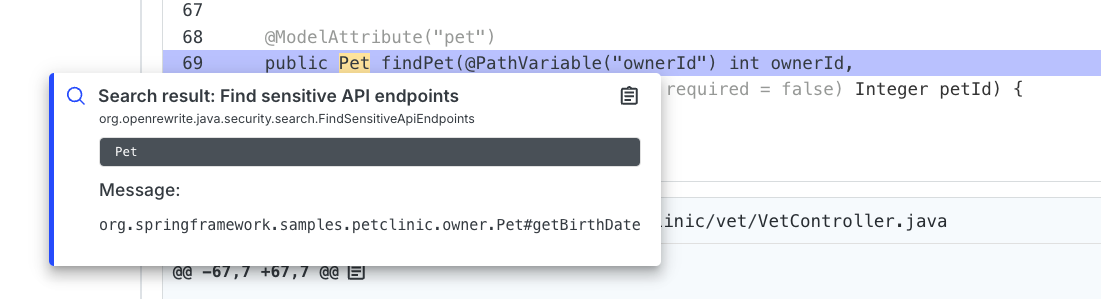
- Clicking on the text that is highlighted will provide you with context about what sensitive data is exposed:
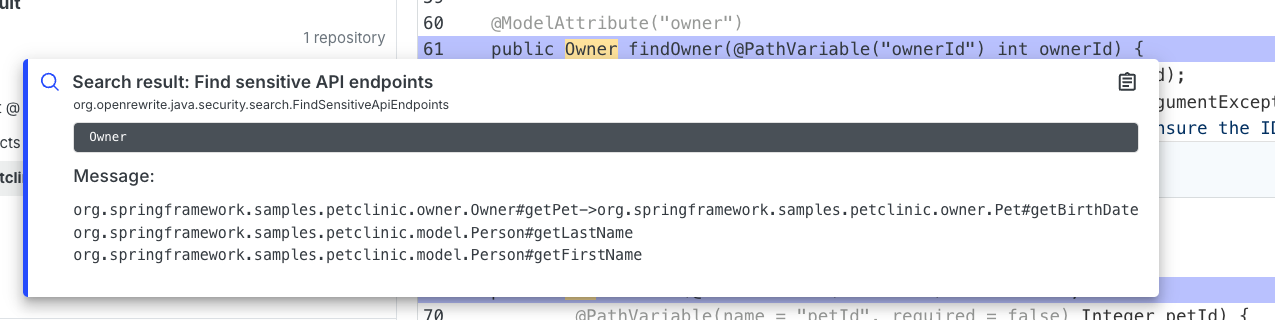
- If you enabled a transitive search, you may find results that step through multiple classes such as in the
Owner->Petexample we discussed above:
If you want to find all outbound API calls that your application is making, you can do so with the find API calls recipe.